Adventures in IPv6 – The Next Generation – Part 2
Part 2 - Configuring The IPSec Tunnel
First thing you’ll need to do is decide whether you’re going to use certificate based or PSK authentication between the ends of the IPSec tunnel, if you decide on certificate based auth, you’ll of course need some certificates, your choice where you get them from, I created an internal CA on my local pfSense box and used that to issue the certificates for my tunnel.
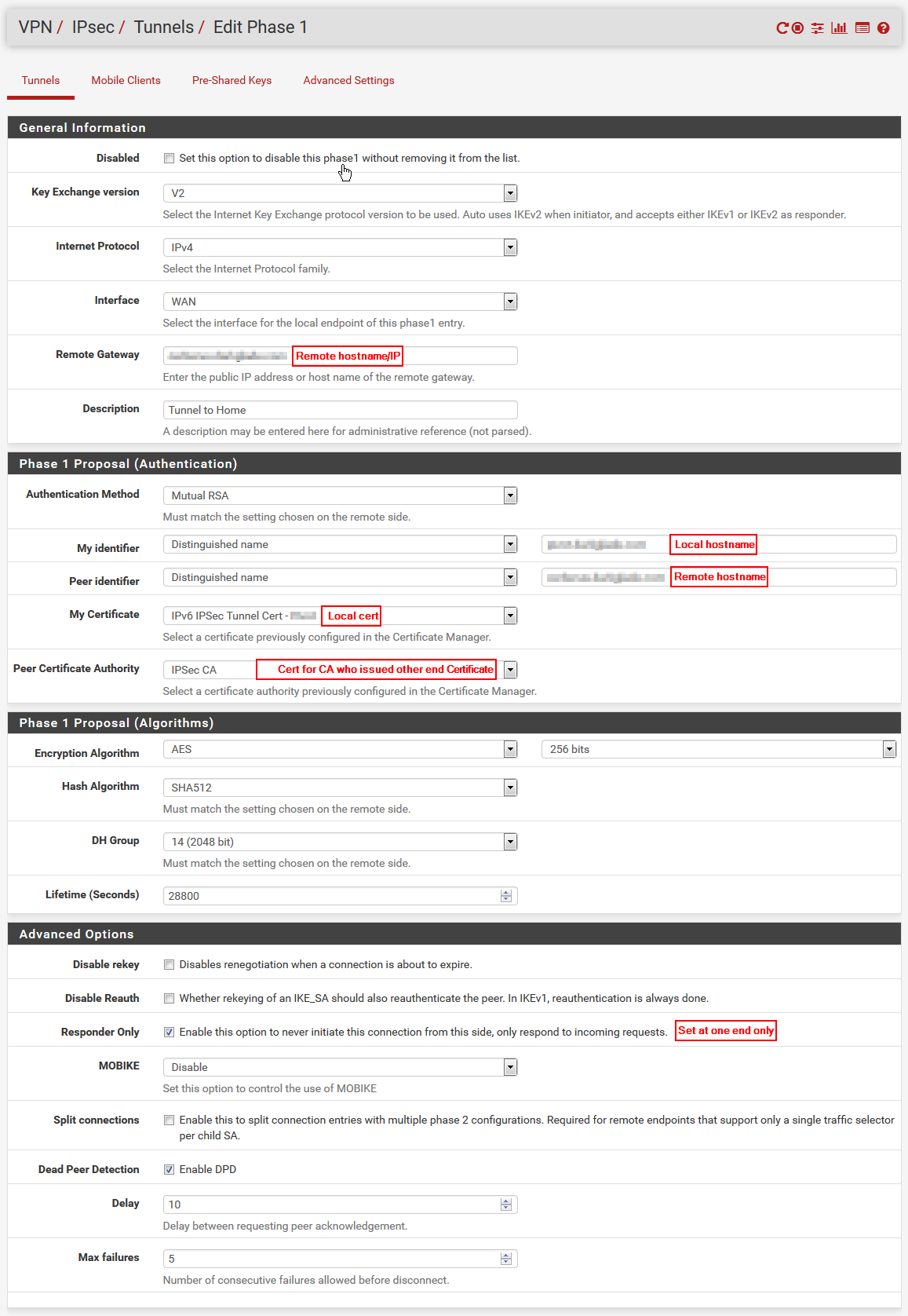
Next step is to configure IPSec Phase 1 (the configurations of each end of the IPSec tunnel are basically mirrors of each other, so I’ll only show one side here);
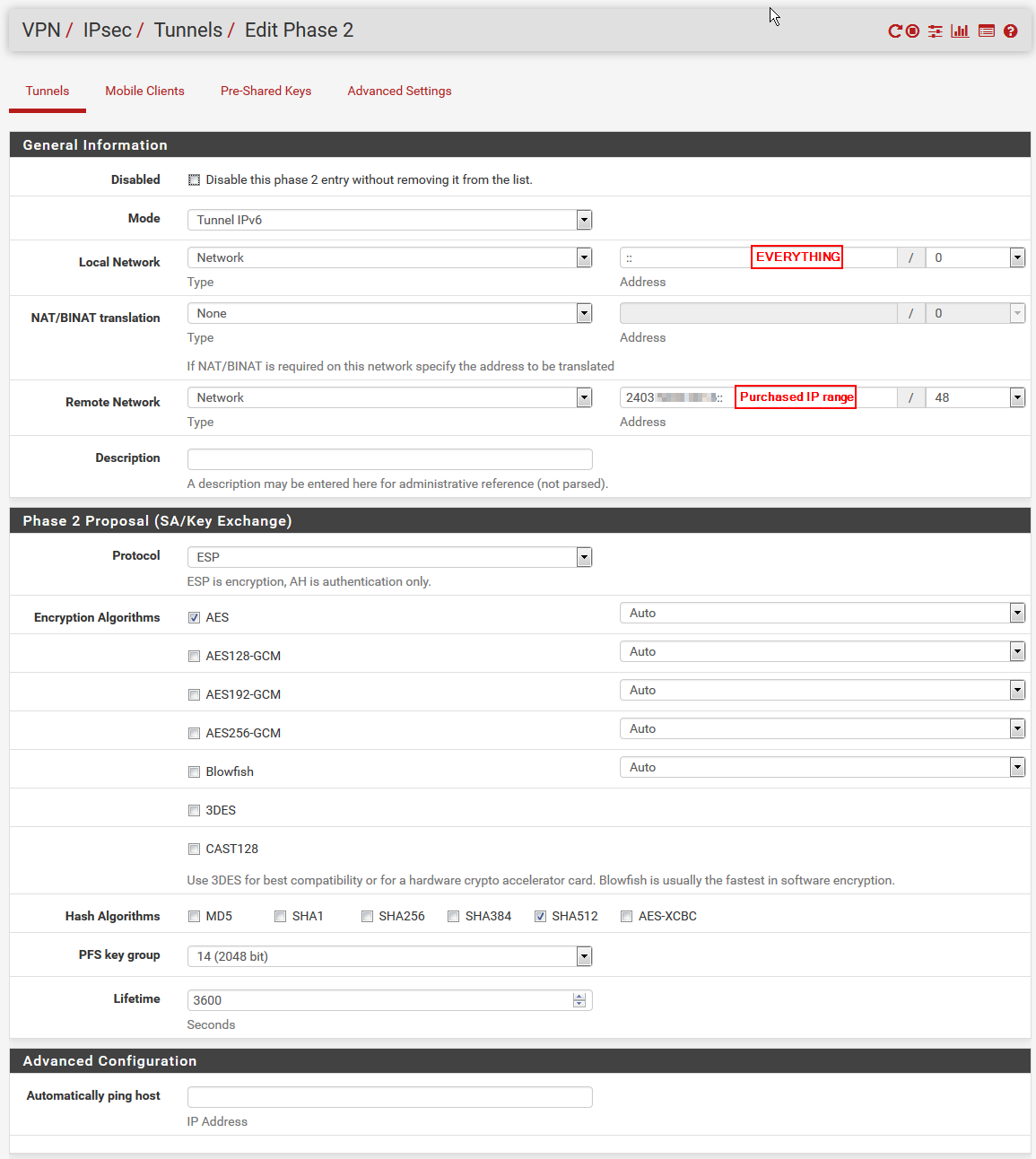
Now onto Phase 2 (again, this is the “outside” host, the “inside” host mirrors this);
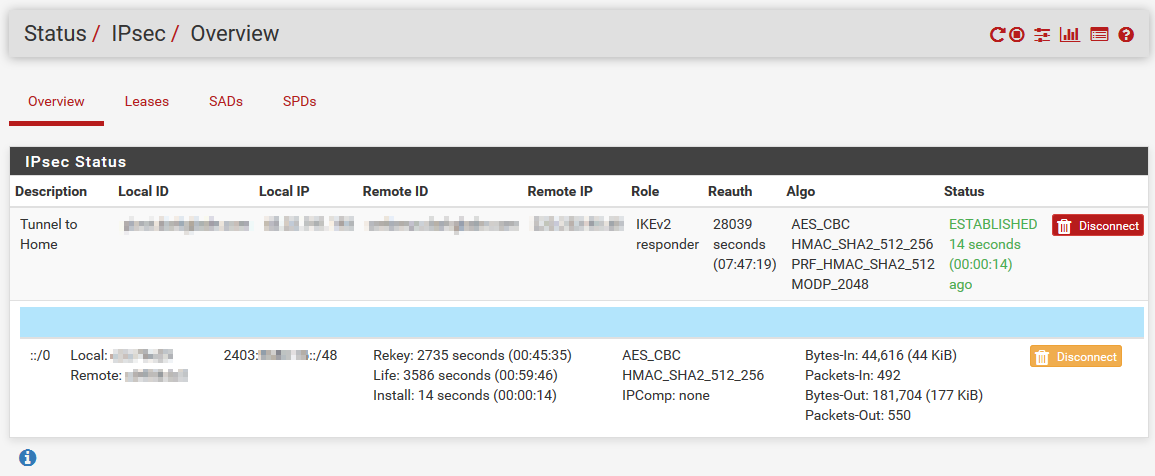
Once that’s done, verify that the tunnel comes up.
At this point you’re largely done and dusted, you need to assign an appropriate IP address (one from your \48) to the LAN interface on your local pfSense box, configure DHCPv6 however you choose, personally I assign the chunk of addresses from ::00FF to ::EFFF to my wired LAN then delegate \62 prefixes out to every other router in my network to dispense as needed, it’s unlikely I’m ever going to have more than 4 subnets behind any of them, should that change in future I can always change the delegation size.
Issues
The config as described here does work, but there’s an issue which seems intractable, inbound connections on IPv6 are fine, connections between “inside” hosts and the “outside” host are fine, connections from my “outside” host and the rest of the world are fine, but connections from “inside” to the rest of the world are excessively slow (~70kB/sec), it seems to be an MSS/MTU issue, I suspect that the IPSec overhead is just too much to do efficient IPv6 encapsulation on my connection.
So for the purposes of exposing internal hosts this is fine (because my end manages MSS at that point), but for actually connecting out to the IPv6 internet it’s not great.
My next step will be to try again with another tunneling protocol that’s lighter weight than IPSec, more on that when I get around to it ;)